Everything You Need to Know About Continuous Diagnostics and Mitigation
GSA Schedule | 3 Min Read

Back in 2010, the Office of Management and Budget (OMB) tasked the Department of Homeland Security (DHS) to lead a government-wide effort to ensure that there were sufficient cybersecurity measures in place for each agency. These security protocols needed to be both risk-based and cost-effective in nature.
Since then, DHS has developed the Continuous Diagnostics and Mitigation Program (CDM) and consistently monitors and adapts the program to make sure it is an asset to government users. The goal of the CDM program is to help bolster cybersecurity methods and to help regulate security monitoring across all federal agencies.
How Does the CDM Program Work?
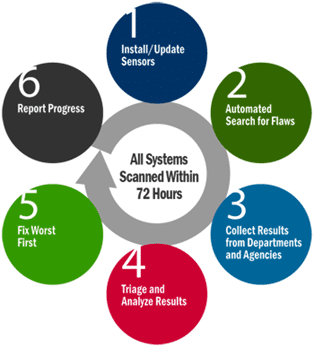
The CDM program is designed to ensure the strength and stability of computer networks and systems when it comes to cybersecurity initiatives. The program helps administrators understand risks to their networks in real time, even identifying and ranking issues as they arise allowing cyber professionals to tackle the most pressing issues first.
This, combined with real time reporting of threats on agency-level dashboards, helps users stay up to date on any cyber risks they may face. Overall the program leads to lowered operational risk with government networks and information security systems.
CDM Program Phases
The CDM program is able to cover fifteen different continuous diagnostic capabilities over three phases: endpoint integrity, least privilege and infrastructure integrity and boundary protection and event management for managing the security lifecycle. Each phase contains the following:
Phase 1: Endpoint Integrity
- HWAM – Hardware Asset Management
- SWAM – Software Asset Management
- CSM – Configuration Settings Management
- VUL – Vulnerability Management
Phase 2: Least Privilege and Infrastructure Integrity
- TRUST –Access Control Management (Trust in People Granted Access)
- BEHV – Security-Related Behavior Management
- CRED – Credentials and Authentication Management
- PRIV – Privileges
Phase 3: Boundary Protection and Event Management for Managing the Security Lifecycle
- Plan for Events
- Respond to Events
- Generic Audit/Monitoring
- Document Requirements, Policy, etc.
- Quality Management
- Risk Management
- Boundary Protection (Network, Physical, Virtual)
Additional Information
- The program has the added benefit of helping federal agencies automate the Federal Information Security Management Act (FISMA) reporting process through automated reports that contain some of the FISMA-required information that can be reported directly to a CyberScope data reporting application which is also managed by DHS.
- The CDM program can manage these tasks through commercial off-the-shelf tools that are updated frequently as threats evolve and change.
- Throughout the CDM program’s development, DHS and GSA have worked together to develop acquisition vehicles on behalf of participants, most notably the CDM Blanket Purchase Agreement (BPA) which is open to all government entities.