CMMC: What Contractors Should Know
Government | Technology | 6 Min Read
Since the Cybersecurity Maturity Model Certification (CMMC) was first announced in 2020, it has undergone several changes. As the Department of Defense (DoD) and other government agencies look to deploy CMMC within government contracting, they will continue to adapt the verification method so it’s more effective.
With all the changes comes confusion, rumors, and just a general struggle to keep up with the latest updates. Last month, we hosted a CMMC webinar with guest speakers Derek White at Beryllium Infosec Collaborative, along with Heather Engel at Strategic Cyber Partners to discuss CMMC and what's important for contractors to know. Here are some highlights from the webinar including CMMC updates, risk management with CMMC, how to prepare for audits, and dispelling false CMMC rumors.
What is CMMC?
The Cybersecurity Maturity Model Certification, or CMMC, was first introduced in 2020 by the Department of Defense (DoD). CMMC was created so government contractors in the Defense Industrial Base (DIB) and beyond can implement the appropriate cybersecurity practices and procedures needed to protect Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
Before CMMC existed, contractors in the DIB oversaw their own cybersecurity practices, resulting in inconsistent levels of protection. CMMC was developed as a unified standard so contractors within the DIB can improve their cybersecurity posture and so their practices are vetted by a certified third party.
Recent Changes and Updates to CMMC
As we mentioned before, CMMC has evolved since it was first introduced, and there have been some changes to the certification and to federal government cybersecurity regulations as a whole.
In May 2020, the White House released an Executive Order on Improving the Nation’s Cybersecurity which affects certain aspects of the CMMC process. Here’s a summary of the relevant information within the order:
- Mandate for agencies to begin to adopt Zero Trust, meaning no one inside or outside the network is to be trusted and verification is required.
- Agencies will review their specific cyber requirements and recommend standard contract language.
- The Federal Acquisition Regulation (FAR) council will also be reviewing cyber requirements and recommending language.
- Federal civilian executive branch agencies must review their unclassified data and identify all areas of sensitivity.
- All contractors (in or out of the DIB) will need to understand how the data they create is stored and transmitted, and how the process fits into the definition of CUI.
In June 2020, the CMMC Accreditation Body (AB) held a town hall that covered several updates including CMMC training, authorized CMMC Third Party-Party Assessor Organizations (C3PAO), and new developments to the CMMC-AB.
Although requirements surrounding CMMC are constantly developing, it’s important to keep up with the current regulations because it will only make it easier to implement any future changes.
Risk Management with CMMC
Risk management is a crucial component of CMMC—but what does it have to do with CMMC exactly?
The cost of working with the DoD has increased considerably in the past decade, and there’s now a minimum cybersecurity standard just to be in the DoD contract system. This is the time to look within your company and identify what your risk tolerance is: can you handle CMMC within your existing infrastructure or does is make sense to outsource it? In order to demonstrate the maturity that will be required with CMMC, you will need to prove that CMMC policy is being followed.
As mentioned above, the DoD is adopting Zero Trust architecture meaning no actor, system, service, or network within or outside the security perimeter is to be trusted. Zero Trust requires continual verification as you move through the network and will require effort on your part.
In orderly to effectively apply these CMMC controls, you should consider conducting a risk assessment to understand what your risk tolerance is and what is standing in your way of executing these requirements.
What Does a CMMC Audit Look Like?
Contractors have a lot of questions about CMMC audits such as: "should I schedule my CMMC audit right now," "should I be contracting with a C3PAO to set up an audit soon," or "when should I plan to have this audit finished?"
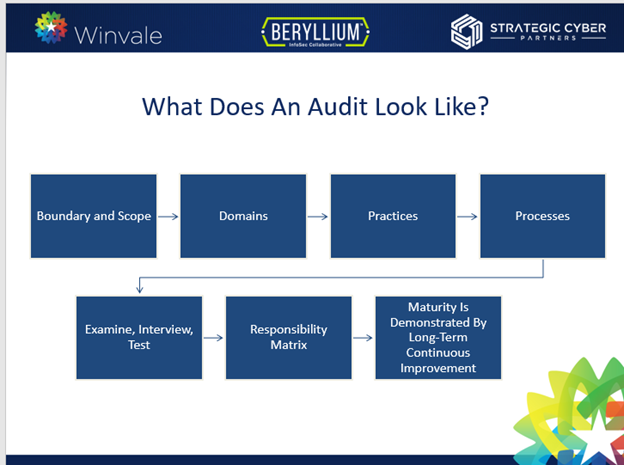
Since CMMC certification audits aren’t available at the time of this article’s publication, there is no reason to rush to schedule your audit at the moment—the first contractors who are going through the audit process first are in the pilot program. However, you can begin preparing for the future audit. This includes understanding what the process looks like and consulting the right resources, while avoiding all misleading information. The graphic below covers the basic outline of the audit process.
What’s important to note about the audit is the certification lasts for 3 years, but that doesn’t mean you are off the hook once you receive the certification notice. It’s a maintained, managed compliance program meaning the whole model is built off continuous improvement. You’ll need to ensure you can identify and mitigate threats as they evolve.
If you want to learn more about the audit process and ways to prepare, you can check out our webinar about CMMC.
The Strategic Plan and Other Process Controls Related to CMMC
CMMC is sectioned out into 5 maturity levels. Not every contractor has to reach level 5, it varies depending on the sensitivity of the data contractors will be working with. Each level has its own set of processes and practices, but defense contractors handling Controlled Unclassified Information (CUI) will need to reach at least maturity level 3, titled processes, or also referred to as the strategic plan.
There hasn’t been much writing about this section of CMMC, but it’s something contractors should be focusing on. Under maturity level control 3.997, each domain must include the following in their plan:
- Document mission and vision
- Outline strategic goals and objectives for implementing the practices
- List references, standards, and relevant procedures
- Identify resources including personnel and funding sources
- Prove buy-in from relevant stakeholders
Strategic planning will encourage contractors within the Defense Industrial Base (DIB) to focus less on checking off requirements and narrow down what they truly want out of this cybersecurity program and how they will manage it.
If you want to learn more about the background behind each maturity level and control, and what each is asking of contractors, the CMMC Assessment Guide is a useful resource.
CMMC Misconceptions
Since CMMC has been developing for a while but hasn’t yet been fully implemented, it’s inevitable that false rumors will spread.
One of the bigger rumors out there is that CMMC is going away completely. NIST 800-171 is not going away anytime soon, and neither is CMMC. As our nation’s network security continues to get compromised and more cyber hacks occur, it becomes increasingly clear how much CMMC is needed as a verification method.
Of course, the model will evolve, especially as the DoD learns and improves CMMC based on the pilot programs. It’s also clear that the “set it and forget it” mentality will not work with CMMC. The DoD already tried that approach with DFARS 7012 and it didn’t pan out.
Another rumor circulating is that you’ll need several different policies, plans, and procedures to succeed under CMMC. That’s not true either. It depends on your organization—for some, it will be easier to have a separate policy and procedure for each domain, but for other organizations especially small businesses, it’s not. There’s nothing in the CMMC regulations that says you need separate documents, it all comes down to what makes sense for your organization.
What’s Next for Contractors and CMMC?
CMMC is going to continue expanding throughout the world of government contracting as the DoD and other agencies begin deploying the verification method. CMMC is expected to be included in non-DoD (civilian) contracts in the future, so it’ll apply to more than just contractors within the Defense Industrial Base (DIB). Even if CMMC isn’t a requirement for you at the moment, it’s important you begin preparing.
If you have questions about CMMC requirements, audits, or the process in general, you can reach out to the Winvale team and we’ll point you in the right direction. If you want more information on CMMC, you can check out these resources:
About Leslie Crowley
Leslie Crowley is a Lead Account Manager for Winvale’s Public Sector department where she manages partner accounts under Winvale’s GSA MAS Large Category F contract. Leslie has vast experience building new business, securing customer loyalty, and forging strong relationships with external business partners.